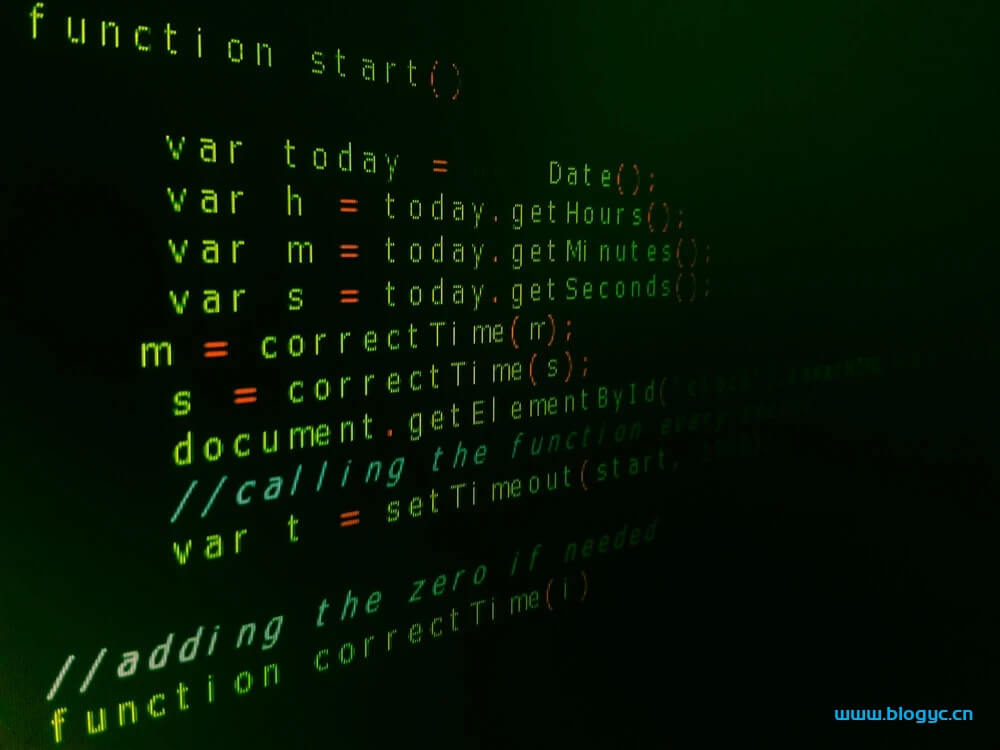
1、服务器WEB目录php后门检查Linux Shell脚本
#!/bin/bash #30 2 * * * /opt/sh/check-eval.sh > /dev/null 2>&1#检查的WEB目录check_path="/data/wwwroot"#日志输出目录check_log="/data/logs"time=`date +%Y/%d/%m/%H:%M:%S`find ${check_path} -name "*.php" -type f -print0|xargs -0 egrep "(phpspy|c99sh|milw0rm|eval\(base64_decode|spider_bc)"|awk -F: '{print $1}'|sort|uniq > ${check_log}/check.logstatus=$(grep php /data/logs/check.log > /dev/null 2>&1)if [ $? -eq 0 ]; then echo "check stauts: ${status} time:$time" exit 0else echo not exist exit 1fi2、服务器上查隐藏进程Linux Shell脚本
#!/bin/bash #30 3 * * * /opt/sh/check-ps.sh > /dev/null 2>&1#查隐藏进程ps_pids="`ps -A | awk '{print $1}'`";for i in /proc/[[:digit:]]*;do if echo "$ps_pids" | grep -qs `basename "$i"`; then : #echo "no found" else echo "Rootkit's PID: $(basename "$i")"; fidoneecho "Chechking Finished,Congratulations to you !!!No found"3、CC攻击导致服务器负载高,根据nginx日志分析单IP大量请求,攻击IP加入iptables防火墙Linux Shell脚本
tail www.aqzt.com.access.log -n 9999 |awk '{print $1}'|sort|uniq -c|sort -rn|awk '{if ($1>200){print $2}}' > /data/nginxlogs/block_attack_ips.log/sbin/iptables -nL |grep DROP | awk '{print $4}' > /data/nginxlogs/iptables.logfilename=`cat /data/nginxlogs/block_attack_ips.log`for ip in $filenamedoif [ `grep $ip /data/nginxlogs/iptables.log` ]then echo "Already exists"else echo "add" /sbin/iptables -I INPUT -p tcp -s $ip --dport 80 -j DROPfidone感谢您的来访,获取更多精彩文章请收藏本站。

© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END


















暂无评论内容